How BitTorrent becomes a DDoS Tool [Hacking]
 A talk at the 27C3 has revealed curtains off a new kind of swarms that can exploit DDoS attacks.
A talk at the 27C3 has revealed curtains off a new kind of swarms that can exploit DDoS attacks.
One of the speakers at Chaos Communications Congress revealed how BitTorrent swarms can be exploited to take down large websites with relative ease under a talk named “Lying To The Neighbours” .
The vulnerability is actually found in the technology that works on trackerless torrents (DHT). Its now possible for someone to trick downloaders of popular files into send thousands of requests to a webserver of choice, taking it down as a result. Effectively turning BitTorrent into a very effective DDoS tool.
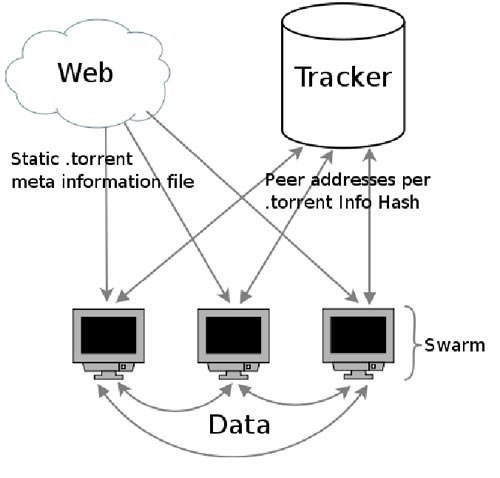
BitTorrent have lived over the years because of their reliability and effectiveness. Unlike a server centric model, where the dependency is on a one server (or distributed servers), its distributed and directly available through individual nodes that auto-discover each other, resulting in faster and more reliable data transfers. This is the reason why, everyday, millions of people (Swarm) use bittorrents to download Terabytes of data.
Hackers have now used the popular DHT technology to abuse BitTorrent downloaders to DDoS a webserver of choice. DHT, under normal operation, discovers peers who are downloading the same files, without communicating with a central BitTorrent tracker. If there are enough peers downloading the same file, this could easily take down medium to large websites. The worrying part is that the downloaders who are participating in the DDoS will not be aware of what’s going on.
These days, DDoS attacks have been in the news regularly, mostly carried out under the flag of Anonymous “Operation Payback”. Initially anti-piracy targets such as the MPAA and RIAA were taken offline, and last month the focus switched to organizations that acted against Wikileaks, including Mastercard, then Visa and Paypal.
The idea of using BitTorrent as a DDoS tool is not entirely new. In fact, researchers have previously shown that adding a webserver’s IP address as a BitTorrent tracker could result in a similar DDoS. The downside of this method is, however, that it requires a torrent file to become popular, while the DHT method can simply exploit existing torrents that are already being downloaded by thousands of people.
Over the next few years, it may actually be able to create non-blockable Torrents. Even today, there are ways of Bypassing torrent blocking, throttling. Now, what remains to be seen is that will BitTorrent developers do enough to fix DDoS vulnerability or will it remain open and cause havoc.
'kisec44 > 2차 심화과정 (Bit torrent + DDOS)' 카테고리의 다른 글
| 토렌트(Torrent) 입문 기초지식 (0) | 2013.01.31 |
|---|---|
| 토렌트 소프트웨어 유용한 팁 (0) | 2013.01.31 |
| 비트 토렌트 관련 문서 (0) | 2013.01.28 |
| BitTorrent가 무엇인가? (0) | 2013.01.28 |
| 비트토렌트(BitTorrent) (0) | 2013.01.28 |